Route Network Traffic With a Route Table
Create a virtual network
In this section, you’ll create a virtual network, three subnets, and a bastion host. You’ll use the bastion host to securely connect to the virtual machines.
- From the Azure portal menu, select + Create a resource > Networking > Virtual network, or search for Virtual Network in the portal search box.
- Select Create.
- On the Basics tab of Create virtual network, enter or select this information:
- Subscription: Select your subscription.
- Resource group: Select Create new, enter myResourceGroup.
- Name: Enter myVirtualNetwork.
- Region: Select East US.
- Select the IP Addresses tab, or select the Next: IP Addresses button at the bottom of the page.
- In IPv4 address space, select the existing address space and change it to 10.0.0.0/16.
- Select + Add subnet, then enter Public for Subnet name and 10.0.0.0/24 for Subnet address range.
- Select Add.
- Select + Add subnet, then enter Private for Subnet name and 10.0.1.0/24 for Subnet address range.
- Select Add.
- Select + Add subnet, then enter DMZ for Subnet name and 10.0.2.0/24 for Subnet address range.
- Select Add.
- Select the Security tab, or select the Next: Security button at the bottom of the page.
- Under BastionHost, select Enable. Enter this information:
- Bastion name: Enter
myBastionHost. - AzureBastionSubnet address space: Enter
10.0.3.0/24. - Enter:
myBastionIPfor Name.
- Bastion name: Enter
- Select the Review + create tab or select the Review + create button.
- Select Create.
Create an NVA virtual machine
- From the Azure portal menu, select + Create a resource > Compute > Virtual machine, or search for Virtual machine in the portal search box.
- Select Create.
- On the Basics tab of Create a virtual machine, enter or select this information:
- Subscription: Select your subscription.
- Resource Group: Select
myResourceGroup. - Virtual machine name: Enter
myVMNVA. - Region: Select (US)
East US. - Availability Options: Select No infrastructure redundancy required.
- Security type: Select
Standard. - Image: Select
Windows Server 2019 Datacenter - Gen2. - Azure Spot instance: Select
No. - Size: Choose VM size or take default setting.
- Username: Enter a username.
- Password: Enter a password. The password must be at least 12 characters long and meet the defined complexity requirements.
- Confirm password: Reenter password.
- Select the Networking tab, or select Next: Disks, then Next: Networking.
- In the Networking tab, select or enter:
- Virtual network: Select
myVirtualNetwork. - Subnet: Select
DMZ - Public IP: Select None
- NIC network security group: Select
Basic - Public inbound ports network: Select
None.
- Virtual network: Select
- Select the Review + create tab, or select Review + create button at the bottom of the page.
- Review the settings, and then select Create.
Create a route table
- From the Azure portal menu, select + Create a resource > Networking > Route table, or search for Route table in the portal search box.
- Select Create.
- On the Basics tab of Create route table, enter or select this information:
- Subscription: Select your subscription.
- Resource group: Select
myResourceGroup. - Region: Select
East US. - Name: Enter
myRouteTablePublic. - Propagate gateway routes: Select
Yes.
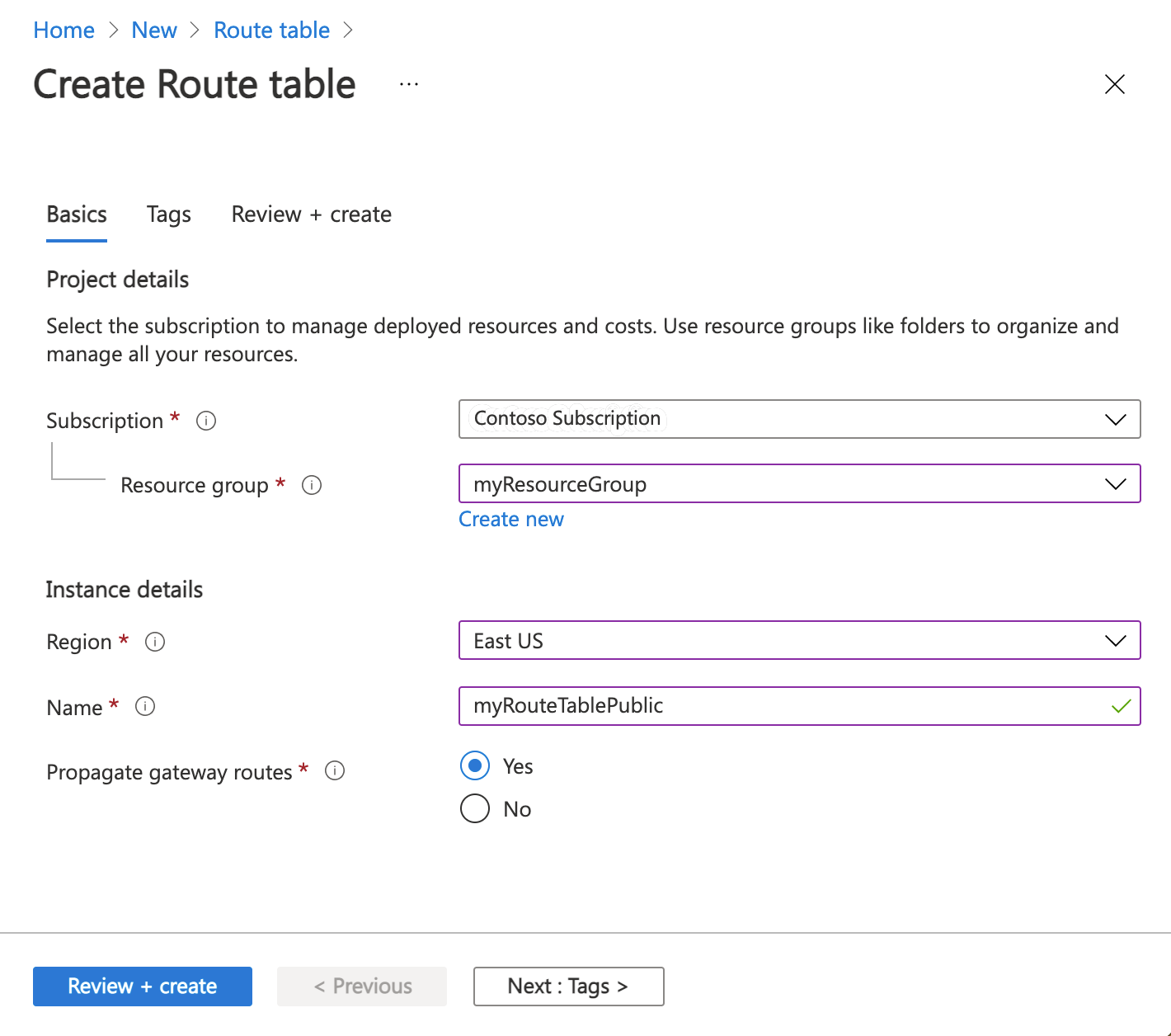
- Select the Review + create tab, or select the blue Review + create button at the bottom of the page.
Create a route
- Select Go to resource or Search for myRouteTablePublic in the portal search box.
- In the myRouteTablePublic page, select Routes from the Settings section.
- In the Routes page, select the + Add button.
- In Add route, enter or select this information:
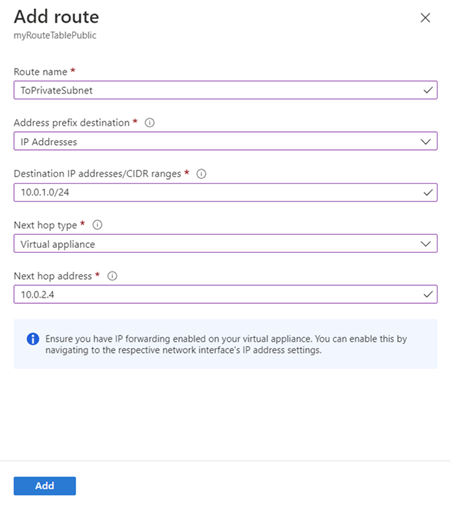
- Select Add.
Associate a route table to a subnet
- Search for myVirtualNetwork in the portal search box.
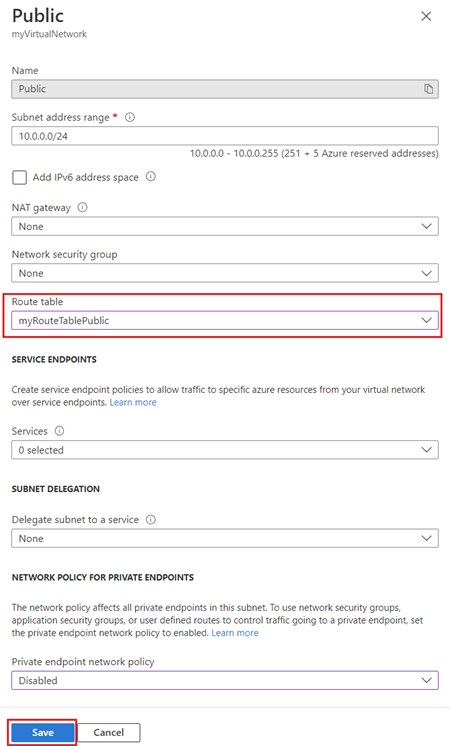
- In the myVirtualNetwork page, select Subnets from the Settings section.
- In the virtual network’s subnet list, select Public.
- In Route table, select myRouteTablePublic that you created in the previous steps.
- Select Save to associate your route table to the Public subnet.
Create public and private virtual machines
Create public virtual machine
- From the Azure portal menu, select Create a resource > Compute > Virtual machine.
- In Create a virtual machine, enter or select this information in the Basics tab:
- Subscription: Select your subscription.
- Resource Group: Select
myResourceGroup. - Virtual machine name: Enter
myVMPublic. - Region: Select (US) East US.
- Availability Options: Select No infrastructure redundancy required.
- Security type: Select Standard.
- Image: Select Windows Server 2019 Datacenter – Gen2.
- Azure Spot instance: Select No.
- Size: Choose VM size or take default setting.
- Username: Enter a username.
- Password: Enter a password. The password must be at least 12 characters long and meet the defined complexity requirements.
Confirm password Reenter password. - Public inbound ports: Select None.
- Select the Networking tab, or select Next: Disks, then Next: Networking.
- In the Networking tab, select or enter:
- Virtual network: Select
myVirtualNetwork. - Subnet: Select Public.
- Public IP: Select None.
- NIC network security group: Select Basic.
- Public inbound ports network: Select None.
- Virtual network: Select
- Select the Review + create tab, or select the blue Review + create button at the bottom of the page.
- Review the settings, and then select Create.
Create private virtual machine
- From the Azure portal menu, select Create a resource > Compute > Virtual machine.
- In Create a virtual machine, enter or select this information in the Basics tab:
- Subscription: Select your subscription.
- Resource Group: Select
myResourceGroup. - Virtual machine name: Enter
myVMPrivate. - Region: Select (US) East US.
- Availability Options: Select No infrastructure redundancy required.
- Security type: Select Standard.
- Image: Select Windows Server 2019 Datacenter – Gen2.
- Azure Spot instance: Select No.
- Size: Choose VM size or take default setting.
- Select the Networking tab, or select Next: Disks, then Next: Networking.
- In the Networking tab, select or enter:
- Virtual network: Select
myVirtualNetwork. - Subnet: Select Private.
- Public IP: Select None.
- NIC network security group: Select Basic.
- Public inbound ports network: Select None.
- Virtual network: Select
- Select the Review + create tab, or select the blue Review + create button at the bottom of the page.
- Review the settings, and then select Create.
Allow ICMP in Windows firewall
- Select Go to resource or Search for myVMPrivate in the portal search box.
- In the Overview page of myVMPrivate, select Connect then Bastion.
- Enter the username and password you created for myVMPrivate virtual machine previously.
- Select Connect button.
- Open Windows PowerShell after you connect.
- Enter this command:
New-NetFirewallRule –DisplayName "Allow ICMPv4-In" –Protocol ICMPv4
- From PowerShell, open a remote desktop connection to the myVMPublic virtual machine:
mstsc /v:myvmpublic
- After you connect to myVMPublic VM, open Windows PowerShell and enter the same command from step 6.
- Close the remote desktop connection to myVMPublic VM.
Turn on IP forwarding
To route traffic through the NVA, turn on IP forwarding in Azure and in the operating system of myVMNVA virtual machine. Once IP forwarding is enabled, any traffic received by myVMNVA VM that’s destined for a different IP address, won’t be dropped and will be forwarded to the correct destination.
- Search for myVMNVA in the portal search box.
- In the myVMNVA overview page, select Networking from the Settings section.
- In the Networking page of myVMNVA, select the network interface next to Network Interface:. The name of the interface will begin with myvmnva.

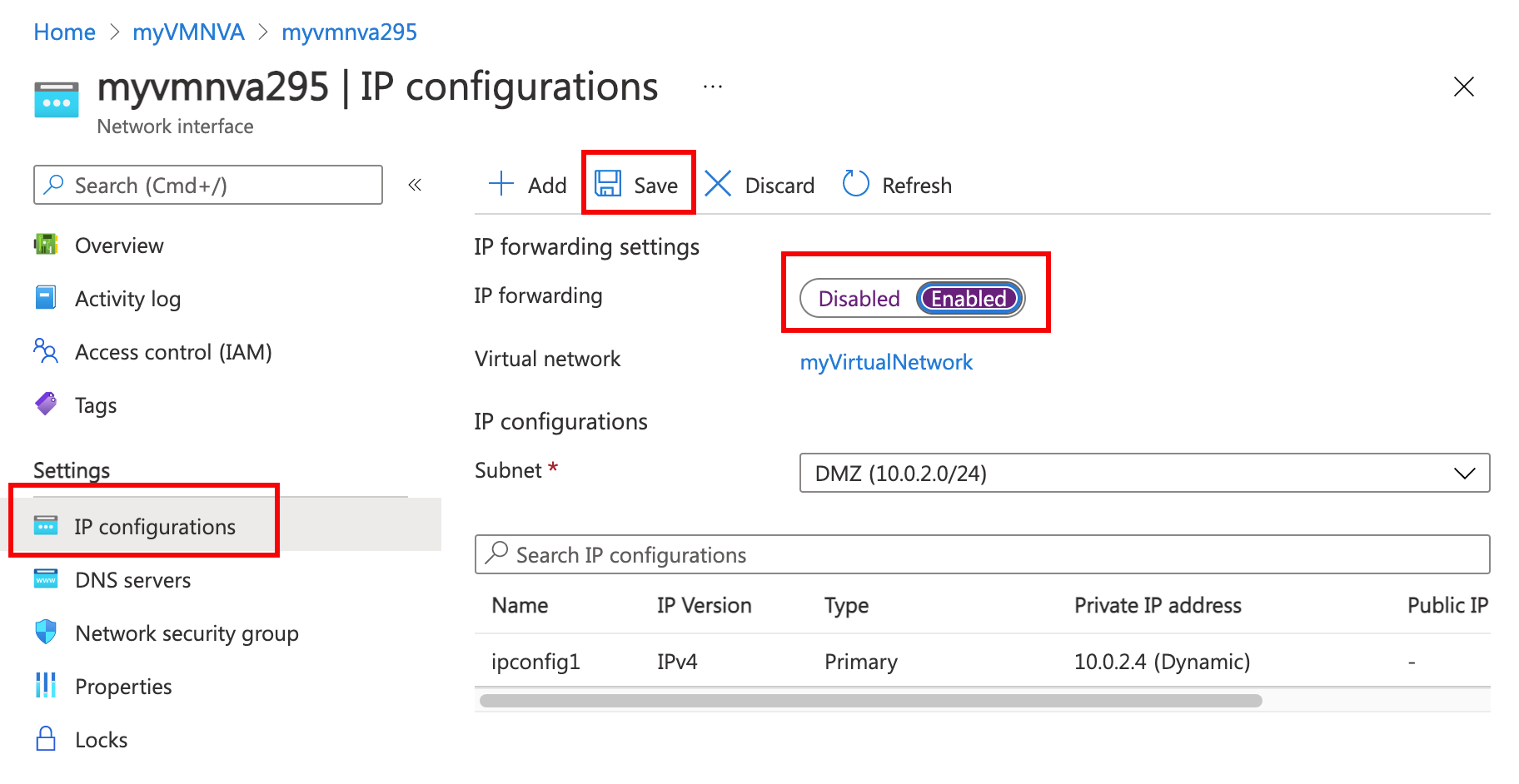
- In the network interface overview page, select IP configurations from the Settings section.
- In the IP configurations page, set IP forwarding to Enabled, then select Save.
Turn on IP forwarding in the operating system
- From PowerShell on myVMPrivate VM, open a remote desktop connection to the myVMNVA VM:
mstsc /v:myvmnva
- After you connect to myVMNVA VM, open Windows PowerShell and enter this command to turn on IP forwarding:
Set-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters -Name IpEnableRouter -Value 1
- Restart myVMNVA VM.
Restart-Computer
Test network traffic from myVMPublic VM to myVMPrivate VM
- From PowerShell on myVMPrivate VM, open a remote desktop connection to the myVMPublic VM:
mstsc /v:myvmpublic
- After you connect to myVMPublic VM, open Windows PowerShell and enter this tracert command to trace the routing of network traffic from myVMPublic VM to myVMPrivate VM:
tracert myvmprivate
You can see that there are two hops in the above response for tracert ICMP traffic from myVMPublic VM to myVMPrivate VM. The first hop is myVMNVA VM, and the second hop is the destination myVMPrivate VM.
Azure sent the traffic from Public subnet through the NVA and not directly to Private subnet because you previously added ToPrivateSubnet route to myRouteTablePublic route table and associated it to Public subnet.
- Close the remote desktop connection to myVMPublic VM.
Test network traffic from myVMPrivate VM to myVMPublic VM
- From PowerShell on myVMPrivate VM, and enter this tracert command to trace the routing of network traffic from myVmPrivate VM to myVmPublic VM.
tracert myvmpublic
You can see that there’s one hop in the above response, which is the destination myVMPublic virtual machine.
Azure sent the traffic directly from Private subnet to Public subnet. By default, Azure routes traffic directly between subnets.
- Close the bastion session.
Tag:Azure